Machine Learning for Red Teams
A comprehensive Machine Learning course for security professionals, focused on practical tooling and adversarial ML, with classical foundations that open the door to Deep Learning and Reinforcement Learning.
OVERVIEW
A comprehensive Machine Learning course for security professionals
If you work in technology, Artificial Intelligence is now the THE topic being discussed. Across all segments of the corporate landscape, AI/ML will proliferate. This course teaches the fundamentals of classical Machine Learning that serve as a foundation, so you can branch into Deep Learning, Reinforcement Learning (RL), Adversarial ML, and other avenues.
By building practical tools, that you can use live in engagements, you will develop a strong understanding of how ML models work and how to code them. Our projects that we have built, and are building present some of what can be accomplished rapidly in cyber security:
- Generative Adversarial Networks for Malware Development
- Clustering Attacks Against XDRs and MDR teams
- Password Hunting with Machine Learning
- Turul: ML evasion C2
- Turul GAN: EDR Evasion Technology
We understand the cross section of ML and offensive security. This was re-enforced by the fact that we were shortlisted for TURUL GAN and TURUL C2 by NATO's Defence Innovation Accelerator in 2024 from 2700 companies across NATO Alliance:

STUDENT FEEDBACK: MLFRT
STUDENT: STEVE SALINAS, LEAD DEVELOPER - Datalytica.net, LLC

"The course presents the most comprehensive review of machine learning, from an introduction to Python to manual algorithm implementation, that I've ever seen. Understanding the intricacies of the manual implementation helped me understand how to better capture the functionality of my own machine learning implementations into OOP abstractions. The operational utility of the method covered in the course is on the bleeding edge of offensive technologies. As AI and ML become more pervasive, the importance of the material in this course will continue to increase."
Training consultants from:
Cybersecurity, financial services, automotive and manufacturing, technology and SaaS, public sector and defense.

Get Certified
CERTIFIED RED TEAM ML SPECIALIST (RTMLS):
The training has three assignments that need to be completed, and handed into our trainers for review. Our team (view here) reviews each coursework submitted and provides feedback. Upon successful completion of all course material, and assignments / coursework you will be awarded the Certified Red Team ML Specialist certification.

This certification will enable you to prove to employers that you can develop tooling such as SharpML, have a deep understanding of Clustering and Classification, and can attack EDRs using ML obfuscation techniques and can use these techniques in both Red and Blue Team.
What You Will Learn
A mixture of videos, exercises, reading, and fully fledged projects will help you master the fundamentals of classical Machine Learning. These techniques are foundational and give you the grounding to branch out into Deep Learning, Reinforcement Learning, Adversarial ML, and other avenues.
Python Basics
Many courses require knowledge of Python - we will teach you from ground-up.
Machine Learning Theory
Learn about Clustering & Classification, the maths behind them, classical ML theory, and how it underpins modern approaches like deep learning.
Adversarial ML
Learn about attacking Machine Learning models - here the focus is on AV & EDR engines static analysis.
Practical Tools
You will learn to build SharpML, and have two other projects to complete.
Foundation and Branches
Classical ML is the foundation. From here you can branch into specialized tracks and advanced applications.
The video lessons are laid out to gradually build your knowledge from the ground up - some videos, some reading, some links, and at the end three practical courseworks that will be assessed before recieving your certificate of completion. The lesson list is below:
Chapter 1
- Introduction. Preview:
Chapter 2: Python
- Install Required Software
- Setting a Workspace
- Basic Program - Hello World
- Scalar Types
- Strings
- Variables
- Tuples
- Lists
- Sets
- Dictionaries
- Indentation
- If Elif Else
- For Loop
- While Loop
- Break Continue
- Defining a Function
- Methods
- Structure
- Using Instances
- Arguments Passing
- Mutable and Immutable
- Standard Library
- Numpy
- Scipy
- Matplotlib Pyplot
- Pandas
- I/O
Chapter 3: Machine Learning Theory and Designing an Algorithm
- Basics - Theory
- Workflow of an ML Algorithm - Theory
- (K-mean) & Distances - Theory
- Class Definition - Practical
- Normalization - Practical
- Outliers Removal - Practical
- Split Data - Training & Test Data - Practical
- Model Selection - Practical
- Score - Practical
- Plot Data - Practical
- Why Not Neural Networks - Theory
Chapter 4: Building SharpML
- SharpML Python Model Code
- Organization of SharpML Code
- Class Set Up
- Load Data
- Load Rules
- Training
- Testing
- Results
- Final Considerations
- Init
- Save Output
- Run
- Examples
- C# Code Overview
- Next Steps
Chapter 5: Build a CMS Web Analyzer
- Intro
- Further
- Instructions
In this course, you'll learn how to develop a model that identifies and classifies web component technologies in static index HTML pages. You'll start by defining the problem, evaluating the pros and cons of using machine learning versus traditional algorithms, and conceptualizing a solution using clustering and classification techniques. You'll then progress to translating this solution into actionable features, scraping relevant data from HTML pages, and compiling a labeled dataset. By the end of the course, you'll have created a high-performance ML model in Python and integrated it into tools like BurpSuite or OWASP Zap. The final project submission will include a comprehensive explanation of your approach and the code you developed.
Chapter 6: Build a Macaronic Obfuscator
- Intro
- Further
- Instructions
In this course, you'll learn how to create a Python tool that obfuscates elements in C# project files to evade detection, based on insights from Advanced Threat Protection (ATP) analysis. You'll begin by setting up your own ATP E5 lab and interfacing with the Anti-Malware Scan Interface (AMSI) through its API and function call interception. Next, you'll generate wordlists from various sources, including Windows OS structures and GitHub directories with malware samples. You'll automate the process of identifying keywords that trigger ATP responses and develop a static obfuscator pipeline to modify these triggers intelligently. Additionally, you'll implement a junk code generation function to evaluate its impact on detection and refine your obfuscation strategy using the AMSI API. The final project submission will include detailed documentation of your approach and the code that performs the obfuscation and analysis.
Chapter 7: LLM Bonus - Build an LLM Infused SAST Tool
- Intro
- Further
- Instructions
- Final Words
In this course, you'll learn to use a local Large Language Model (LLM) that integrates with a secure code regex tool to identify, explain, and dynamically suggest fixes for potential code issues. You'll start by deploying Llama.cpp locally and experimenting with various open-source LLMs to determine the most suitable one. You'll then adapt a tool like cq to highlight vulnerable code, use Control Flow Graph generators to enhance context, and prompt the LLM with identified code and its surrounding context. Finally, you'll integrate the entire workflow into a web app with an HTML dashboard, combining LLMs, static code regex tools, and CFG generators to identify and explain potential security vulnerabilities in large codebases. The final project submission will include detailed documentation and the code that performs these actions, tested against specified repositories.
For a more detailed explanation of the course, don't hesitate to reach out to us and ask any questions you have.
Who Is it for
| Your starting point | How the course will feel |
|---|---|
| You already build ML models and write C# implants | Mostly review; only the adversarial/obfuscation angles will stretch you. |
| You’re an experienced red-teamer / pentester who has scripted but hasn’t touched ML | Sweet spot – the ML side ramps up gently, then the projects push you. |
| You’re early-career (OSCP-level) and still shaky on Python / AD tradecraft | Expect a steep learning curve once you hit the SharpML and obfuscation sections; it will feel advanced. |
| You’re a blue-teamer/data-scientist looking to understand attacks | The offensive perspective will be new and challenging, but the ML won’t. |
What You Will Build
1. Main Project - SharpML:
SharpML employes C# to mine Active Directory file shares, while bundling a resource file. This resource file is a custom Machine Learning algorithm written in Python (compiled with Pyinstaller) whose logic uses Clustering and Classification to evaluate the likelihood of a User / Password pair combinations and subsequently automatically test these against a Domain Controller to assist operators in identifying passwords littered on fileshares.
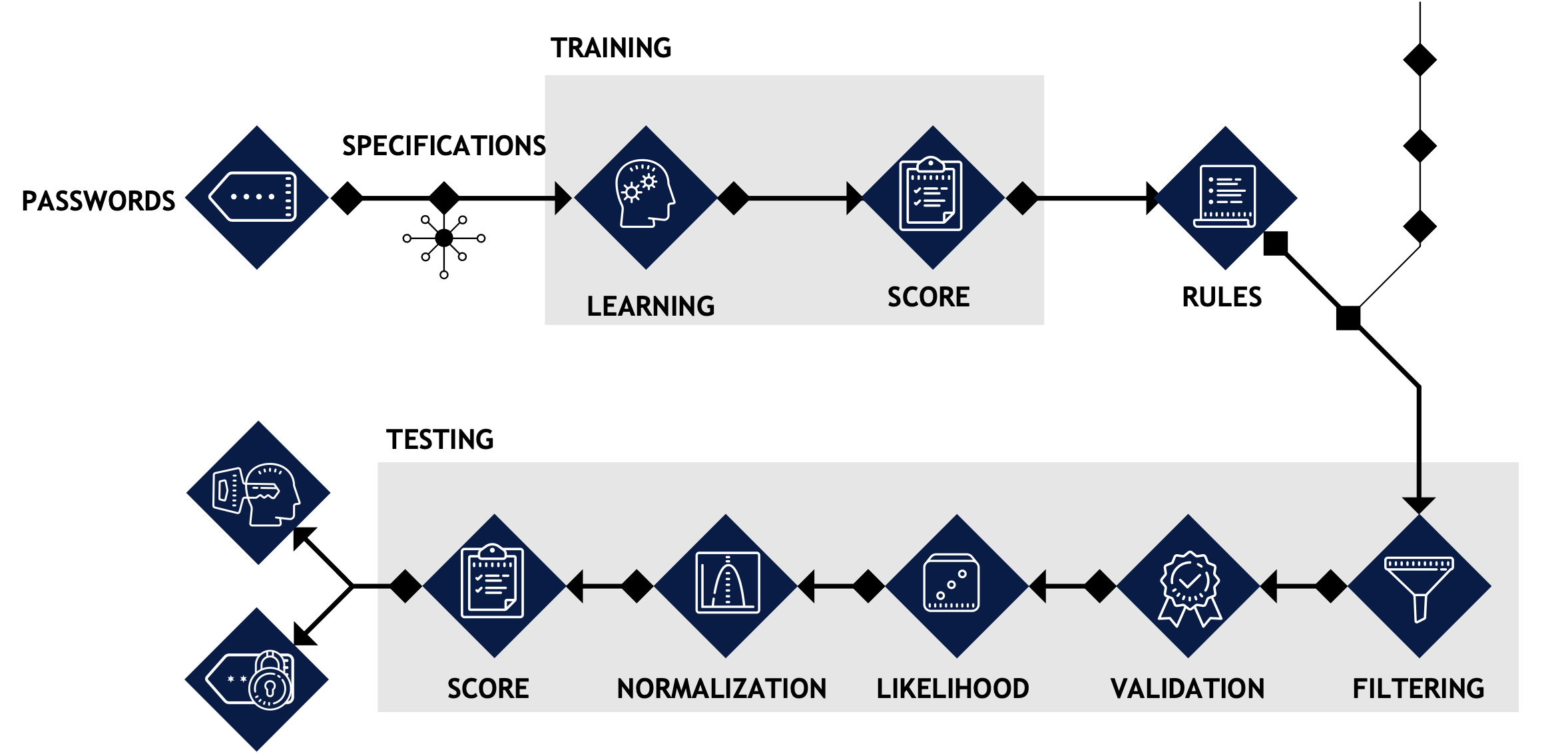
Open-source tool
SharpML Codebase
Browse the repository tree and preview files without leaving the page.
A version of this tool had been open-sourced when the team were running Hunnic Cyber but further developments have been made internally by Atlan Digital R&D and you will recieve the umcompiled Machine Learning model as part of the training. (This project was also mentioned in conjunction with DeepPass developed by the eminent Harmj0y at SpectreOps; View here) and discussed by Cobalt Strike in the context of post exploitation: View here.
2. Macaronic Obfuscator for Static Evasion
You will build and train your own obfuscator for static evasion.
3. CMS Web Technologies Analyzer
Generating a dataset yourself, you will develop a model to identify web technologies in HTML pages.
4. LLM for Secure Code Review
As part of the course you build your own secure codre review tool using LLMs.
By enrolling you agree to the Terms & Conditions.
ENQUIRIES
Whether you represent a corporate, a consultancy, a government or an MSSP, we’d love to hear from you. To discover just how our offensive security contractors could help, get in touch.
General Enquiries
+44 (0)208 102 0765
enquiries@atlan.digital
86-90 Paul StreetLondon
EC2A 4NE
New Business
Tom Kallo
+44 (0)208 102 0765
tom@atlan.digital
