Consulting Services
We provide a range of top flight security consulting services, focused on bespoke vulnerability identification and security penetration testing across the technology, people and process layers.
Select a section, then expand it to read more details.
Key service offerings
We help organisations validate real-world resilience, reduce time-to-detection, and ship safer systems through high-fidelity security testing and targeted engineering support.
Use the services index above to jump into the specific engagement type you need, from adversary simulation to LLM security evaluation.
Adversary simulation & Red Team
Full-spectrum red team engagements, methodologies, and controls assessed.

Adversary simulation & Red Team
Full-spectrum red team engagements, methodologies, and controls assessed.

Metric-Centric, Repeatable Approach
Our consultants have experience delivering on regulated adversary simulation engagements under the CBEST, TBEST, TIBER-EU and other frameworks, so we understand threat intelligence led security testing.
Our adversary simulation capabilities are designed for organizations with extremely high threat profiles, where realism, control and repeatability are non-negotiable.
What We Test
We can mount attacks against the People, Process and Technology layers in full spectrum threat actor simulations where the following controls are assessed:
Perimeter Controls
- Employee Security Awareness and Phishing resilience
- Email Filtering
- Email Anti-Spoofing Mechanisms
- DNS Filtering
- Web (HTTP / HTTPS) Filtering
- Network Filtering
Workstation Controls
- Workstation Hardening
- Antivirus / Anti-Malware
- Application Whitelisting
- Protection of PrivilegedAccounts - Local Administrators
- Application Security Settings
- Employee Laptop Protection
Internal Controls
- Malicious Network Activity Detection
- Monitoring and Incident Response
- Protection of Privileged Accounts - Domain Administrators
- Protection of Privileged Accounts
- Protection of Service Accounts
- Domain Security Policy
- Data Loss Prevention
- Patch Management Policy
- Weak Password Policy
- Network Segregation
Cyber High-Level Methodology
Our methodologies are mapped to the MITRE ATT&CK framework, where we are delivering bespoke engagements for clients, but typically follow a six step model working our way from out to in, to fully assess operational impact. Our tooling and activity in the six steps:
1. Recon
Profiling, SharpInfo Pretexts, OSINT
2. Exploitation
Phishing, EDR Evasion, Command Execution and C2 Callback
3. Privilege Escalation
Active Directory Enumeration, Workstation & Network Share Enumeration – patch levels, password policy, file shares, Active Directory Certificate Services (ADCS)
4. Lateral movement
SharpHound, AzureHound, Certify, WinRM, RDP, AdXplorer, SharpML, SharpSniper.
5. Persistence
Registry, WMI, VPN, Scheduled Tasks, COM, ‘Living off the land’, DMZ Web Shells.
6. Operational impact
Comprehensive Reporting and Presentation around business and operational impact.
Identity-Based Red Teaming (2025/2026)
Identity control planes now define blast radius. We test how attackers chain identity, SaaS, and cloud trust to move laterally without noisy infrastructure compromise.

IdP & SaaS Control Plane
Assess identity provider configurations, SaaS admin surfaces, and governance gaps that enable persistence.

Privilege & Trust Pathing
Map trust relationships, service principals, and role sprawl across hybrid estates to expose escalation paths.

Token & Session Security
Test session lifecycle controls, conditional access, and token hygiene to reduce identity-driven lateral movement.
Operator Tooling & R&D
Our R&D is embedded in this work: we operate our own Turul GAN and Turul C2 stack, and we build bespoke tooling for mission-specific tradecraft. Explore our R&D program.
Turul C2 + Turul GAN
Turul C2: Our operator-focused command-and-control framework with encrypted beaconing, malleable profiles, and inbuilt evasion to support controlled, high-fidelity simulations.
Turul GAN: GAN-driven code transformation for C# payloads to preserve functionality while reducing static EDR detection, powering repeatable testing and custom toolchains.
See the R&D deep dive and demos: Turul C2, Turul GAN, video demo.
Physical Intrusion Methodology
When performing Red Team assessments in the United States, or where our client requires a physical component, our methodology is outlined below.
1. Recon
Planning, Long and Short Range Reconnaissance
2. Preperation
Operational Planning, Intelligence Review, Resourcing
3. Mobilisation & Staging
Suit Up, Test equipment, Comms, Deploy
4. Manoeurver Operations
Environmental Conditions, Observation, Cover & Concealment, Signaling
5. Strike and Penetrate
Character Change, Movement, Establish Position, Execution, SITREP, Mission Standing.
6. Operational impact
Comprehensive Reporting and Presentation around business and operational impact.
Infrastructure Penetration Testing
Network, infrastructure, and cloud testing with a four-phase approach.

Infrastructure Penetration Testing
Network, infrastructure, and cloud testing with a four-phase approach.

Network, Infrastructure & Cloud
Whether you are a digital asset provider with some Azure cloud infrastructure, or an international telecoms organisation with hundreds of thousands of public IPs, we can thoroughly assess your network infrastructure (on-prem or cloud) with expert level attack coverage.
We cover hybrid estates across AWS, Azure, and GCP, focusing on exposed services, identity pathways, segmentation gaps, and cloud control-plane misconfigurations that drive real-world risk.

On-Prem Infrastructure
Assess routing, segmentation, legacy services, and internal attack paths across critical systems.

Cloud Environments
Test cloud posture, identity controls, storage exposure, and control-plane security in AWS, Azure, and GCP.

Hybrid Attack Surface
Validate cross-environment pivots, VPN and SD-WAN boundaries, and shared identity trust.
-
Scope
Atlan Digital R&D works with you to develop a detailed scope of the penetration testing to be undertaken.
-
Recon
In the first phase Atlan Digital R&D will perform OSINT, analysing the routing mechanisms, and then all your systems will then be scanned for all active TCP and UDP ports and we will establish the security rule-base.
-
Exploit
In the exploitation phase Atlan Digital R&D will iteratively identify and exploit vulnerable systems using public vulnerability information, and configuration & design errors. A scenario analysis over the entire network will is conducted.
-
Report
In the final phase Atlan Digital R&D will perform comprehensive reporting of the issues identified. The risks will be rated according to numeric CVSS scores alongside an internal qualitative risk grading.
Web Application Penetration Testing
OWASP/PTES-informed testing across application layers and controls.

Web Application Penetration Testing
OWASP/PTES-informed testing across application layers and controls.

360° Coverage on Web Application Pen Tests
Enterpise applications, e-commerce platforms, trading systems, SasS platforms and other web first components dominate the corporate landscape. We work to comprehensively assess their security posture for known and unknown security vulnerabilities.
Methodology
Our methodology is built upon the PTES (Penetration Testing Execution Standard) and the OWASP TOP 10 Framework but also informed by our teams experience of conducting 100s of application tests.
Fingerprinting
Mapping web app, hosts, content scripts and files by looking at the supporting infrastructure Source code analysis, developer commands, client side validation, applet and class decomplication.
Platform Enumeration
Exploit known OS and application vulnerabilities Attempt to use default insecure configurations.
Application Functionality
Circumvent application normal processing by conducting parameter poisoning, directory traversal and XXE HTML form modification, SQL command insertions, unauthorized database access, database corruptions.
Authentication
Cookie examination, session re-use, sensitive cached information Intrusive account testing is performed at the end including brute forcing user accounts and password attacks.
Reporting
Comprehensive reporting risk rated by both CVSS3 and Atlan.
LLM Penetration Testing
Security testing for LLM applications and frontier model risks.

LLM Penetration Testing
Security testing for LLM applications and frontier model risks.

Application Security & Frontier Model Safety
We provide dedicated security testing for LLM applications and frontier models, combining red teaming methodologies with application security review to identify model misuse, data exposure and control failures.
LLM Application Security Testing
Prompt injection, data exfiltration, tool abuse, retrieval risks, agent workflow manipulation and guardrail bypass testing for production LLM applications.
LLM AppSec Review
Threat modelling, access control verification, RAG pipeline review, prompt and system message analysis, and evaluation of output filtering and monitoring.
Frontier Model Testing
Safety red teaming, misuse pathway discovery and evaluation of jailbreak resilience, autonomy risks and high-impact capability safeguards.
Model Evaluation & Governance
Evaluation harness design, red team scenario planning, policy testing and reporting aligned to organisational risk governance.
Mobile Penetration Testing
Android and iOS testing methodology from planning to dynamic analysis.

Mobile Penetration Testing
Android and iOS testing methodology from planning to dynamic analysis.

Mobile Application – Android & iOS
As an extension of web applications, mobile applications can allow extended funcionality - whether as a transcation signing mechanism, custom 2 factor authentication solutions, thick clients providing business critical functions - we inspect these applications at the deepest levels.
OWASP Top 10 – Mobile
While specific techniques exist for individual platforms, a general mobile threat model is used by Atlan Digital R&D in creating a mobile security testing methodology for any platform. The outline below describes this general mobile application testing methodology.
Prerequisites/Planning
Tasks and requirements before conducting the mobile security assessment.
Information Gathering
The steps and things to consider when you are in the early stage reconnaissance and mapping phases of testing as well as determining the application’s magnitude of effort and scoping.
Static Analysis
Analyzing raw mobile source code, decompiled or disassembled code.
Dynamic Analysis
Executing an application either on the device itself or within a simulator/emulator and interacting with the remote services with which the application communicates. This includes assessing the application’s local inter-process communication surface, forensic analysis of the local filesystem, and assessing remote service dependencies.
ICS Penetration Testing
SCADA and critical infrastructure assessments with staged testing.

ICS Penetration Testing
SCADA and critical infrastructure assessments with staged testing.

Industrial Control Systems (SCADA)
Critical infrastucture provides much of the backbone of a city's, or even a country's successful operational ability. In troubling times, these systems can be high priority targets for nation states, or advanced cyber criminal groups. We can apply our methodologies to help identify weak points and security risks to allow you to mitigate them.
-
Scope
- Define business purpose of engagement
- Determine sensitivity of business functions and processes
- Create and agree ICS business process model
- Confirm specific systems, devices and infrastructure in scope
- Confirm composition of testing team
-
Assess
- Gather threat intelligence
- Conduct threat modelling exercise
- Determine major vulnerabilities
- Assess risks and priorities
- Agree risk-based approach to testing
-
Discovery
- Conduct ICS device discovery exercise
- Determine network topology
- Gather and review ICS network and device configuration information
- Create and agree ICS technical infrastructure mode
-
Test Plan
- Create test scenarios
- Determine offline and online tests
- Determine resource requirements
- Create and agree progressive test schedule
-
Live Testing
- Undertake and document offline and online tests
- Analyse test results and consolidate findings
- Document ICS environment remediation recommendations
- Review findings with key stakeholders
Secure Code Review
Manual and automated review across modern stacks and SDLC guidance.

Secure Code Review
Manual and automated review across modern stacks and SDLC guidance.

JavaScript, Ruby, Infra as code, NodeJS, Python, .NET, C/C++
Finding security vulnerabilites before applications reach deployment stage is critical. We can work with your developers collaboratively to bake in security or even help you develop a Secure Development Lifecycle (SDLC).
Secure Code Review:
Reviews are performed in alignment with industry proven best practices, guidelines and standards from organisations such as OWASP, MITRE, CERT and NIST. A general threat model is used by Atlan Digital R&D when conducting source code reviews for complex enterprise applications.
Prerequisites/Planning
Evaluating tasks and requirements for conducting the code review, as well as assessing the application’s magnitude and scope of effort required.
Static Analysis
Analysing raw source code, using manual techniques and automated scanners that highlight code hotspots.
Developer & Architect Interviews
We will work closely with the developers where appropriate to expediate the process of understanding the code, understanding the architecture of the application and providing knowledge transfer.
Information Gathering
Review of all the application’s supporting documentation and development guidelines. This allows consultants to identify the intended purpose, functionality and development approach.
Dynamic Analysis
Working in combination with static analysis using human and automated resources; we will also perform dynamic analysis of the code, in the event the code is unreachable statically or where efficiency is improved dynamically.
Software Development
Custom security tooling, ML-enabled capabilities, and bespoke development.

Software Development
Custom security tooling, ML-enabled capabilities, and bespoke development.

Custom Software, Machine Learning & Tooling
With many of our consultants having contributed to the security community, or having been full time developers themselves, we can respond to requests to develop programmatic solutions where cyber security domain knowledge is essential.
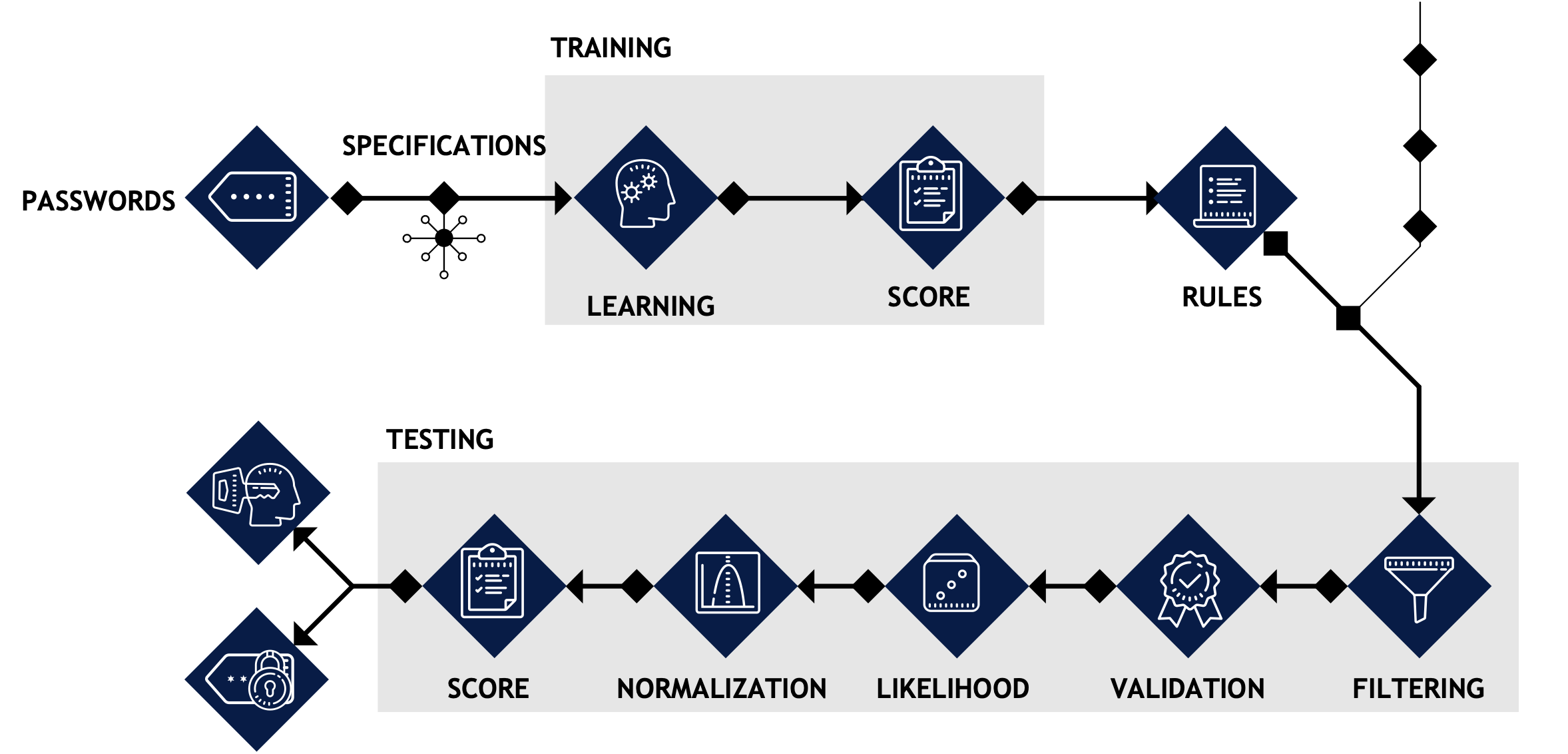
Example Capability - SharpML:
SharpML employes C# to mine Active Directory file shares, while bundling a resource file. This resource file is a custom Machine Learning algorithm written in Python (compiled with Pyinstaller) whose logic uses Clustering and Classification to evaluate the likelihood of a User / Password pair combinations and subsequently automictically test these against a Domain Controller to assist operators in identifying passwords littered on fileshares.
A version of this tool had been open sourced by the consultants when at Hunnic Cyber but Version 2, wherein further developments have been made internally by Atlan Digital R&D can be requested. The write up for this project can be viewed here. Our current research outline around building a Generative Adversarial Network for Malware Development can be viewed viewed here.
Penetration Testing
We can develop solutions to complement our manual testing activities to enable a client to be tested 24/7, 365 days of the year.
Red Team & Malware Development
We can assist clients or other consultancies in developing tooling to enhance security testing activities.
Machine Learning & Automation
As part of our consulting efforts we can develop solutions to help automate security tasks, continuous security scanning tools or apply machine learning to security problem solving.
ENQUIRIES
Whether you represent a corporate, a consultancy, a government or an MSSP, we’d love to hear from you. To discover just how our offensive security contractors could help, get in touch.
General Enquiries
+44 (0)208 102 0765
enquiries@atlan.digital
86-90 Paul StreetLondon
EC2A 4NE
New Business
Tom Kallo
+44 (0)208 102 0765
tom@atlan.digital
